October is Cyber Security Awareness Month!
Each and every one of us needs to do our part to make sure that our online lives are kept safe and secure. That's what Cybersecurity Awareness Month - observed in October - is all about!
This year's theme is Do Your Part, #Be Cyber Smart. Here are tips to help you stay cyber secure.
This is no joke! Do You Know What Kind of Data You are Working With?
Protecting UCSC Data
When dealing with UCSC data, keeping it secure is a top priority. Compromised or leaked data can lead to disastrous consequences involving shame, regret, and a ridiculous number of lawyers. This is no joke.
Defining P1, P2, P3 and P4 Data - what is it?
- P1 data encompases Hours of Operation, Parking Regulations, Course Catalogs, Press Releases, and Public Websites.
- P2 data includes Business Records and documentation not containing P3 or P4 data (email, calendar, meeting notes), research using publicly available data, UC directory info (where no FERPA block is requested), and Building Plans.
- P3 data consists of Student Education Records (protected by FERPA), IT Security Information and Plans, UC Personnel Records, and other confidential information.
- P4 data includes Financial Records, Credit Card, Financial Aid, Payroll, Personally Identifiable Info (PII), Social Security Numbers, Electronic protected health information (ePHI), and other highly sensitive information.
Guidelines to handling UCSC data
Start Here
Before even thinking about working with UCSC data, you must comply with minimum security standards for any devices connected to UC networks or working with UC data. This applies to all protection levels (P1-P4 data). If you have any questions, submit a ticket to SlugHub for assistance.
Accessing P3-P4 Data
Before accessing P3-P4 data, ensure that you have the proper authorization and training. It is important to know what kind of information is P3-P4 data so you know how to handle it. Visit Data Protection to find out more about what types of information falls under these categories.
Protecting UCSC Data
When it comes to storing information, make sure the location is authorized for the protection level of the data.
- Google Apps are approved to store P1-P3 but NOT P4 data
- Slack is only approved to hold P1-P2 data
- Asana is only approved to hold P1, P2, and P3 data level (excluding PII)
- UC provides storage methods to handle the security for you, learn more about Data Center storage options.
- For any non-UC approved storage options, you are responsible to ensure all security controls are in place.
Refrain from taking and sharing screenshots, faxing, or printing when possible. All hard copies should be stored in locked environments. All digital files must be encrypted whether they are being transmitted or at rest.
Sharing the Data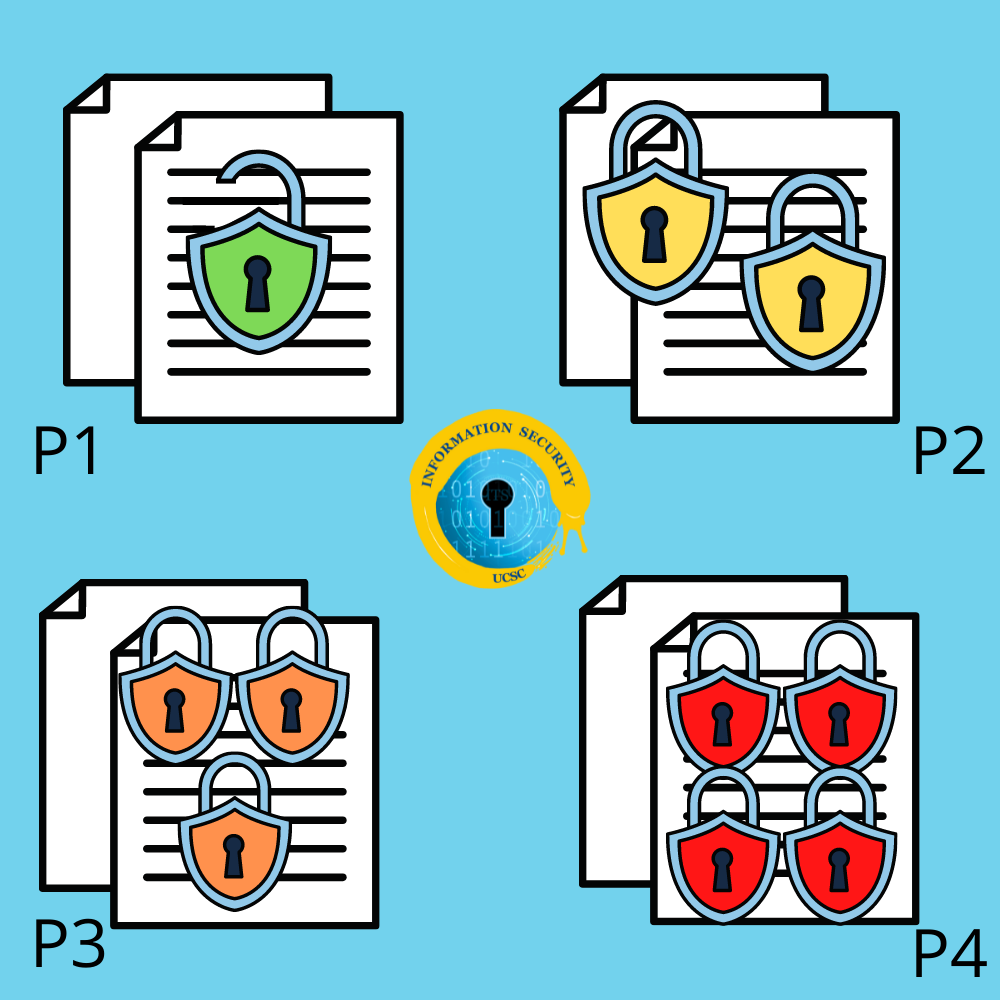
- When sharing P3-P4 data first be sure that the person you are sharing it with is authorized to access this information.
- Do not forward, add to, or respond to an email message with P3-P4 information and read the whole email before sending it. If the person you are contacting does not need the data, do not share it with them.
- When transmitting P3-P4 data contact the ITS Support Center for secure file transfer options. Do not share over unencrypted wireless. Use eduroam when on campus and campus VPN everywhere else.
- A great way to prevent accidental sharing of information is to share data via Google Drive. This allows you to control who can see the data through the document share settings rather than relying on email recipients.
Disposal
Whether you are disposing of hard copies of data or removing data from a device you are getting rid of, the procedure is the same. Data must be disposed of immediately when it is no longer in use. For more information, refer to UC Institutional Information Disposal Standard.
Reporting
First and foremost you must report all security incidents, known or suspected, to ITS regardless of the type of data and your authorization. The sooner Information Security is aware of an issue, the sooner we can address and mitigate any impacts. Visit the Report a Security Incident to learn what counts as a security incident and how to report it.
Failure to Protect P3-P4 Data
Failure to comply and follow security rules for protecting P3-P4 data could result in serious consequences. Students and employees trust us with their data, we not only risk the privacy of these individuals but also fines, lost data, reputational risks, and more. If P4 data is inappropriately released, CA state law requires the individual that the data pertains to be officially notified.
Resources
Confidentiality of Electronic Research Data
HIPAA Security Rule Information
Habitu8 Explains Stuff - Clean Desk Policy by Habitu8, The Security Awareness Video Company (1:07)

