Protect Passwords
Protecting your passwords is essential to help prevent unauthorized access to your accounts and safeguard sensitive data, such as financial details and private messages. Neglecting password security can expose you to identity theft, fraud, and compromise your online privacy.
Create Strong Passwords
Passwords should be:
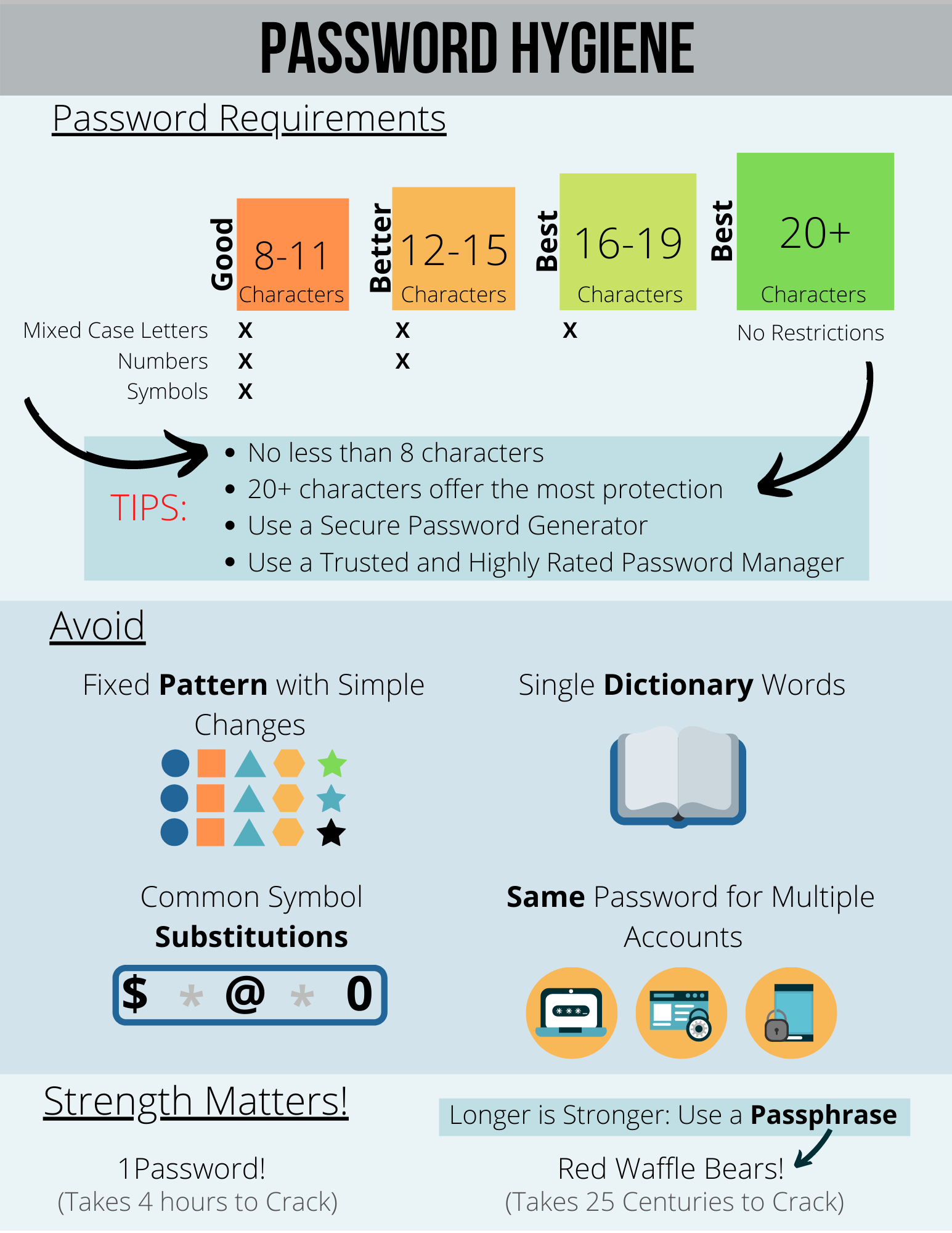
- At least 8 characters long with a mixture of upper- and lower-case letters, numbers, and symbols.
- 12-15 characters with a combination of mixed case letters and numbers.
- 16-19 characters with mixed-case letters.
- 20 characters of any kind.
UC recommends passwords between 16-25 characters, also known as passphrases. A strong passphrase may consist of:
- Several words separated by spaces. This can be easier for you to remember but hard for anyone else to guess.
- A few memorable, unrelated words, as illustrated in this cartoon.
Passwords and Passphrases should NOT:
- Be a complete dictionary word,
Your username or login, - A child's name, a pet's name, a birthday, or anything else easily guessable.
Kaspersky's password strength checker can help gauge the strength of a password and show you how easily it can be hacked (Do NOT enter your actual password).
Keep Passwords Secret
The following practices will help keep your passwords secure:
- Use different passwords for different accounts. Also, use different passwords for work and non-work.
- Don't reveal your passwords to anyone, including co-workers and supervisors. ITS will never ask you for your password. Neither should any reputable service provider.
- Avoid writing your passwords down. If you need to write your password down on paper, safeguard the paper in a locked drawer or cabinet rather than on or under your monitor/keyboard, or in a drawer near your computer!
- Use a Password Manager to store passwords. Click here for a list of the best password managers.
- Change initial passwords, password resets, and default passwords the first time you log in. These passwords can be extra vulnerable to guessing or hacking.
- Ensure that passwords are transmitted securely. Before logging in to a web site, look for "https" (not http) in the URL to indicate that there is a secure connection.
Use Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA), also known as two-step or 2-factor authentication, adds a second layer of protection to your UCSC account in addition to your username and password. This extra layer prevents anyone but you from logging in to your account, even if they know your password. MFA is required for access to UCSC services using the CruzID Gold password login.
Examples of MFA include:
- use of a one-time code in addition to a password, typically sent via text, app, or voice when you want to log in;
- thumb scans (biometrics);
- lockouts after several incorrect login attempts;
- Google's two-step verification;
- Duo push notifications for mobile devices. Click here to enroll.
For more information, refer to the following University of California Policies and Standards:
(Back to Minimum Requirements Main Page)

