Introduction to IS-12: UC's IT Recovery Policy
What Is IS-12?
IS-12 is UC's IT recovery policy. It establishes requirements and role-based responsibilities for creating an IT recovery plan for UC Santa Cruz institutional information and IT resources in the event of an emergency.
IS-12 Requirements
According to IS-12, IT recovery planning requires:
- Alignment with UCSC's Business Continuity Plan (BCP).
- Oversight by a Cyber-Risk Responsible Executive.
- Adoption of a risk-based approach.
- Maintaining an inventory of institutional information and IT resources.
- Recovery Level Classification of institutional information and IT resources.
Role-Based Responsibilities
IS-12 specifies the recovery-planning responsibilities of the following roles:
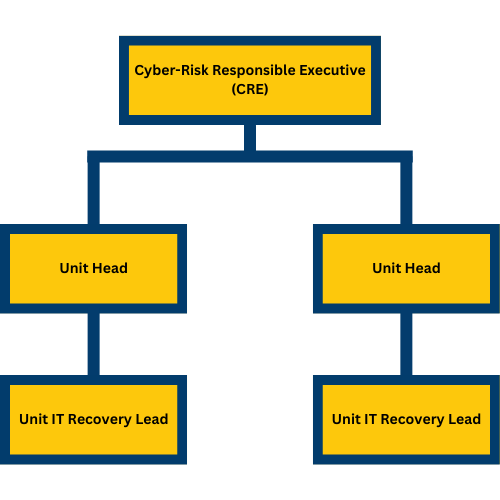
The Cyber-risk Responsible Executive (CRE) is responsible for approving the IT recovery plan. CREs appoint an IT Recovery Lead for the university.
Unit Heads are responsible for Unit IT Recovery Planning, appointing Unit IT Recovery Leads, and ensuring the creation of Unit IT Recovery Teams. Unit Heads appoint Unit IT Recovery Leads (UITRLs).
Unit IT Recovery Leads (UITRLs) ensure that IT Recovery planning and testing take place. They communicate requirements to key parties and coordinate the execution of the plan in the event of an emergency.
Unit Information Security Leads (UISLs) ensure that the planning and execution of IT recovery includes meeting security requirements.
Compliance
Compliance with IS-12 can be achieved by full compliance, in which CREs and Unit Heads meet all the requirements of this policy, or iterative compliance, a multi-phased model of compliance that must:
- Assess the initial state of IT recovery readiness.
- Review risks and compliances.
- Plan and implement improvements.
- Assess progress (annually, at minimum).
Exceptions
While exceptions to an IT recovery policy or standard may weaken UCSC's ability to withstand a disaster, they are occasionally necessary and permitted. Units must follow a risk-based approach when requesting an exception to the controls specified in parts IV, V, and VI of the IS-12 policy. Exception requests must follow the UCSC-approved exception process.

